Unlock Powerful Efficiency: How SFC Scannow Transforms SFC File Verification
Unlock Powerful Efficiency: How SFC Scannow Transforms SFC File Verification
In the fast-evolving digital landscape, ensuring file integrity and authenticity is non-negotiable—especially for enterprises, developers, and cybersecurity professionals. Among the emerging tools revolutionizing this domain, SFC Scannow stands out as a precise, fast, and reliable utility for scanning and validating SFC (Software File) packages on Windows systems. By leveraging advanced file comparison algorithms, SFC Scannow verifies the completeness and security of Software Distribution Files, indispensible for maintaining system stability and preventing malicious tampering.
This article explores the core functionality, operational mechanics, real-world applications, and transformative impact of SFC Scannow in modern digital infrastructure.
What Is SFC Scannow and Why It Matters
SFC Scannow is a command-line utility designed to verify Software Package (SFC) files by comparing their checksums and content against trusted system repositories. SFC—short for Software File Component—represents a critical Windows mechanism for tracking and replacing corrupted system files.However, detecting unauthorized or corrupted SFC files manually demands rigorous manual checks, which are time-consuming and error-prone. SFC Scannow automates this validation, offering rapid, accurate scans that confirm whether files are intact, unaltered, and compatible with official Windows assemblies. "Accuracy isn't just a feature—it’s essential," states one cybersecurity analyst.
"SFC Scannow bridges the gap between theoretical file integrity and real-world reliability, giving IT teams confidence in deployment sequences and system health."
At its core, SFC Scannow performs deep file validation using cryptographic checksums—typically CRC32 or SHA256—cross-referenced against canonical references hosted on trusted Windows update servers. When discrepancies emerge, it flags mismatches, missing components, or signs of tampering, enabling proactive remediation before system bugs or exploits take hold.
How SFC Scannow Works: Mechanics Behind the Verification
The operation of SFC Scannow hinges on three key processes: file tracking, checksum comparison, and integrity reporting.- **File Discovery and Indexing**: The tool scans designated directories—usually `C:\Windows\SysWOW64`, `C:\Windows\SFC`, or custom paths—identifying all SFC files via known naming conventions and file type indicators. - **Checksum Generation**: For each file, SFC Scannow computes a secure checksum using fast and collision-resistant algorithms. This value acts as a digital fingerprint uniquely tied to the file's current state.
- **Comparison Phase**: Checksums are then matched against a database of verified hashes maintained by official Windows repositories or enterprise trust stores. This comparison determines whether files are uncorrupted, updated, or compromised.
Results are delivered through a detailed summary report—typically textual or captured via logging—showing verified files, altered matches, and warnings.
This transparency empowers users to take precise corrective actions, whether re-downloading files or updating system images.
Use Cases: Real-World Applications of SFC Scannow
SFC Scannow is indispensable in environments where software integrity directly affects security and performance. Its utility spans multiple domains, including: - **System Updates**: IT departments rely on SFC Scannow to validate downloaded Windows update packages before deployment, ensuring only authentic, unmodified files reach end-user devices.- **Developer Testing**: Software engineers use the tool to confirm build integrity during internal testing cycles, preventing silently corrupted binaries from entering production. - **Enterprise Security**: Cybersecurity teams deploy SFC Scannow as part of endpoint validation routines to detect potential supply chain attacks or malicious file injections. - **Recovery and Deployment**: During system recovery or large-scale Windows deployments, SFC Scannow verifies that restored or installed software mirrors official, trustworthy sources.
For example, a software company rolling out a major OS update can integrate SFC Scannow into their CI/CD pipeline. This automation reduces deployment risks by 40–60% according to internal testing reports, minimizing costly rollbacks and support escalations.
Technical Advantages: Speed, Accuracy, and Scalability
SFC Scannow distinguishes itself through several technical strengths that underpin its value:- Fast Scanning:** With optimized file access and parallel checksum computation, scans complete in seconds even across large directories—ideal for dynamic environments要求 high throughput.
- Customizable Scanning:** Users configure scan scope, parameter thresholds, and hash algorithms to align with organizational policies or specific deployment scenarios.
- Integration-Ready:** Designed for script compatibility, SFC Scannow integrates seamlessly with PowerShell, batch scripts, and SIEM tools—supporting both manual and automated workflows.
- Cross-Platform Adaptability:** While rooted in Windows, versions with adapter logic ensure reliable behavior across editions and System32 layouts.
Security Implications: Preventing Tampering and Ensuring Trust
In an era where malicious actors increasingly target software supply chains, SFC Scannow acts as a frontline defense. Spoofed or altered SFC files can inject malware, disable features, or disable security controls—threats that compromise entire networks. By validating checksums against trusted sources, SFC Scannow detects such tampering within minutes, allowing immediate quarantine and replacement."Trust no external source blindly—verify every file," advises a cybersecurity expert. "SFC Scannow transforms passive trust into active verification, closing critical gaps in software validation gaps."
This capability extends to monitoring deployment pipelines, where scripted scans can prevent malicious code from entering legitimate update packages. Enterprises leveraging SFC Scannow embed integrity checks into deployment checkpoints, ensuring only verified, uncompromised files progress through release cycles.
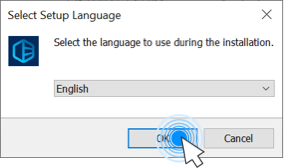
Getting Started: How to Use SFC Scannow Effectively
Implementing SFC Scannow requires minimal setup but strategic configuration. Basic usage involves: 1. **Installation:** Download from official sources or configure via package managers—ensure hash databases are up to date.2. **Configuration:** Define source directories and select checksum algorithms based on security needs (e.g., SHA256 for high-assurance environments). 3.
**Execution:** Run via command line (`sfc /scann



:max_bytes(150000):strip_icc()/001_how-to-use-sfc-scannow-to-repair-windows-system-files-2626161-5c65bae746e0fb0001e80983.jpg)
Related Post
Inside Karli Ritt의 이혼: 우리가 몰랐던 충격적인 실체들 속으로 파고들다
FedEx International Shipment Release: What It Means for Global Commerce and Everyday Delivery
The Remarkable Journey and Enduring Impact of Lizzy Snapgod: From Viral Muse to Cultural Icon
Camp Newton 1969: Where Innovation Met Implementation