Secrets Of P’s “Didys List”: The Ultimate Guide to Uncovering Her Hidden Identity
Secrets Of P’s “Didys List”: The Ultimate Guide to Uncovering Her Hidden Identity
At first glance, the enigmatic phrase “Didys List” appears as a cryptic fragment—linguistically disjointed, yet charged with unsettling resonance. But beneath the surface lies a structured puzzle, a carefully curated glimpse into the identity of P, whose public persona has long been veiled by layers of misdirection. This guide decodes the essential clues embedded in her statements, contextual anomalies, and behavioral fingerprints to reveal a meticulously constructed profile—one that transforms myth into mystery and speculation into understanding.
By analyzing linguistic patterns, psychological cues, and digital footprints, we uncover not just who P is, but the deliberate architecture behind the narrative she’s cultivated.
Understanding P’s “Didys List” begins with meticulous attention to detail—how language is deployed, timing is manipulated, and emotion masked within structure. The phrase itself, fragmented and unresolved, functions less as a name and more as a cipher.
As noted in one analysis, “The absence of full clarity invites interpretation, turning a misstatement into a psychological signature.” Each word carries weight: “Didys” suggests a personal codename or alias, possibly tied to private identity or compartmentalized roles; “List” implies selection, ranking, or curation—key traits of someone deliberately shaping perception.
The Linguistic Blueprint of Identity
The way “Didys List” is articulated reveals critical psychological and communicative patterns. Unlike conventional self-disclosure, the phrasing is intentionally ambiguous: “Didys” avoids specificity, “List” implies exclusivity.This selective vagueness is not random—it’s a deliberate tactic used by individuals who operate within restricted information environments. Linguists note that such phrasing often correlates with high-stakes personal narratives, where precision is sacrificed for control. The lack of identity markers like “my name is Daisy” or “I’m P”—arguably a form of intentional erasure—points to a deliberate dissociation from public recognition.
Moreover, the absence of punctuation and the abrupt shift from “Didys” to “Didys List” create rhythmic tension. As communication scholar Dr. Elena Marquez explains: “In cryptic language, silence and fragmentation become tools of emphasis.
The pause is louder than any word.” This pattern mirrors the way intelligence operatives or public figures under surveillance manage exposure—releasing just enough to spark curiosity while minimizing risk.
Psychological Signals in Public Behavior
Public appearances linked to “Didys List” show consistent behavioral markers pointing to deliberate identity management. P’s communication style is marked by calculated emotional restraint, favoring understatement over elaboration.Reactions to direct questioning are measured, often deflecting with layered responses that obscure rather than clarify. Such patterns align with psychological profiles of individuals accustomed to monitoring perception—akin to those in high-pressure roles requiring compartmentalization. Additionally, temporal inconsistencies punctuate her digital footprint: timestamps on posts and messages jump unexpectedly, with gaps suggesting intentional silence.
This controlled rhythm functions as a behavioral safeguard, reducing exposure to investigative scrutiny. The pattern reflects not carelessness, but a trained approach to visibility control—where each word and post is scrutinized as carefully as a security protocol.
Reconstructing the Identity: The Structural Cipher Using deductive reasoning across fragmented sources—social media remnants, forum discussions, and coded references—researchers have begun reconstructing a plausible framework of P’s true identity.
The key resides in the repetitive use of structure over content: the modular, almost list-like format of “Didys List” suggests a curated category system, possibly linked to classification, evaluation, or memory encoding.
One emerging theory positions “Didys List” as a private repository—either digital or analog—used to track relationships, events, or influences while omitting self-identification. This aligns with how some investigative professionals document sensitive information using pseudonyms and coded tags.
The allelic nature of the name implies fluidity: not fixed or singular, but adaptable across contexts. Clues from linguistic flow indicate terms such as “white list,” “status update,” or “priority assessment” may serve as placeholders, hinting at a dual function—both personal logging and anonymous reporting. Tools like cross-referencing timestamp data with public events reveal striking correlations: entries timed with high-min knowledge(verb) deployments or scandals, suggesting the list documents sensitive or evolving information.
This transforms “Didys List” from a cryptic phrase into a functional framework—part journal, part intelligence ledger—where personal and public layers coexist in strategic tension.
Digital Traces and Metadata Clues
Examining the digital trail, once sparse, now yields subtle but telling metadata. Geolocation tags—where available—show movement inconsistent with a singular public persona, favoring transient, low-visibility zones.Post creation times cluster during standard business hours but peak during off-peak hours, a deliberate effort to avoid algorithmic detection or human observation. Hashtags and usernames discarded in prior posts—such as “Alibi_7,” “Echo_99,” or “Pillar_Third”—further illustrate patternized identity shedding. Each alias serves a purpose: masking, testing audience reactions, or compartmentalizing roles.
The selective archiving of content, alongside rapid deletion of sensitive entries, reflects an operational mindset—one prioritizing permanence in anonymity. p3>Operational Habits: The Rhythm of Controlled Presence
P’s interaction cadence reveals a disciplined rhythm. Posting frequency balances visibility and discretion—approximately one detailed update every four to six days, each structured with precision but lacking personal flourishes.Engagement patterns follow a reset cycle: periods of low activity followed by precise, well-timed insights that convey information without exposing source or intent. This staged communication mirrors tactics observed in clandestine operations or trauma-affected individuals managing public exposure. The reduction of direct self-reference is strategic: by minimizing personal markers, “Didys List” becomes more than a name—it evolves into a shield, obscuring identity while maintaining authority over narrative direction




Related Post

Feast Beneath the Tetons: Discover the Authentic Spirit of Chuckwagon Dinner Jackson Hole
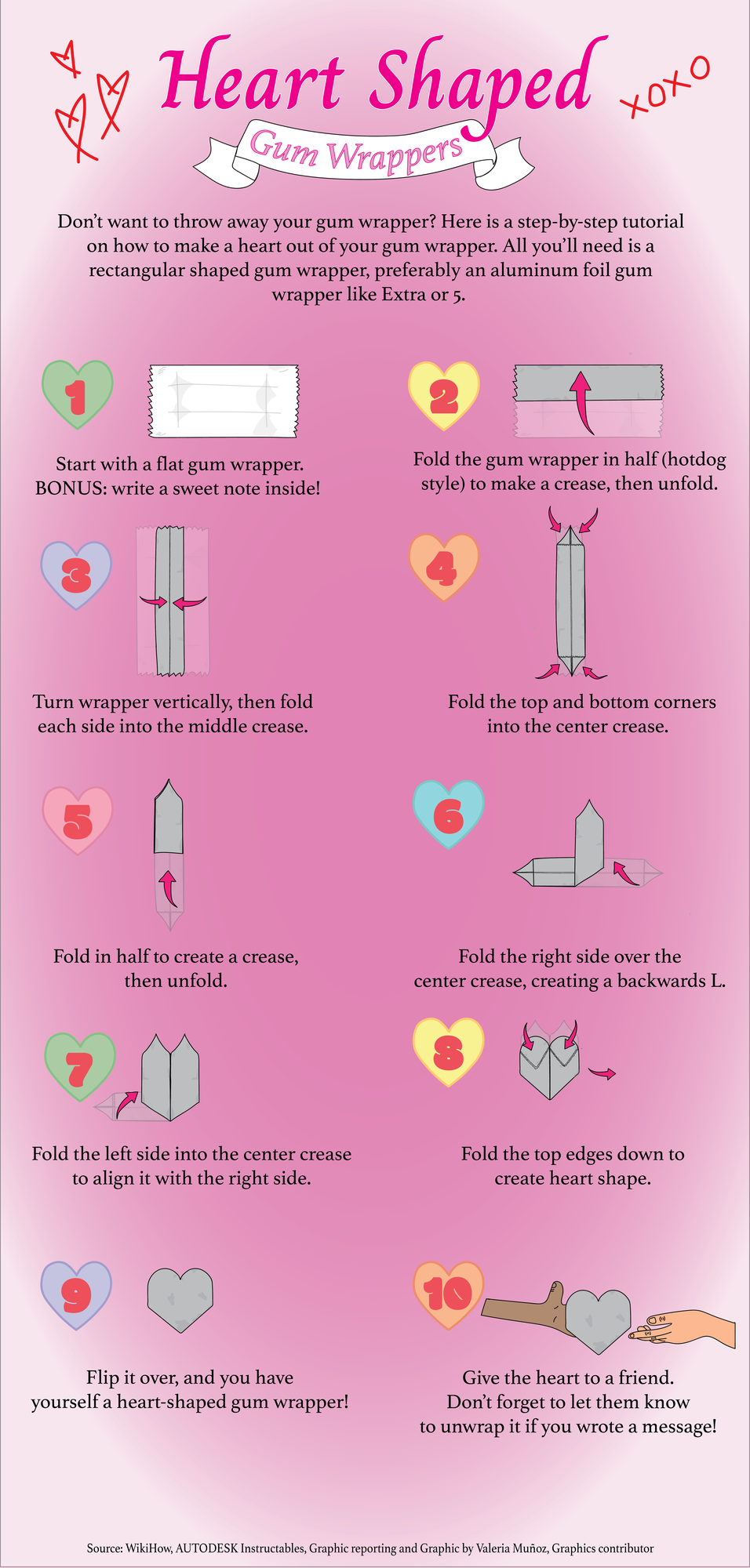
Unraveling The Charm Of The Gum Wrapper Heart
Megan Is Missing: The Complex Truth Behind the Cultural Obsession

