How to Find Your iPhone Instantly Using Find My iPhone Log In
How to Find Your iPhone Instantly Using Find My iPhone Log In
In an age where smartphones are extensions of our lives, losing an iPhone can feel like losing a piece of identity—especially when access to critical data hinges on being able to remotely activate or locate the device. The Find My iPhone Log In process stands as a powerful yet often underutilized tool, enabling users to regain control, unlock the phone, or pinpoint its location with precision. Whether the device is misplaced, stolen, or simply out of sight, mastering the steps to log in via Find My iPhone empowers timely recovery and peace of mind.
At the core of this capability is Apple’s Find My network, a global infrastructure designed to track and secure lost or forgotten devices. When activated through a verified iCloud account, Find My iPhone allows authorized users to remotely access the device—whether by locking it, erasing data, or awakening it. But accessing this functionality requires a secure login, typically via a unique session generated during setup or recovery.
Understanding how this log-in process works, its technical foundations, and real-world utility is essential for anyone reliant on iPhones.
The Mechanics Behind Find My iPhone Log In
How Secure Remote Access Is Enabled
Apple’s Find My system relies on encrypted communication between the lost iPhone and iCloud servers. To log in, users account for two critical elements: a valid Apple ID linked to the device and a secure session token generated during a prior login or setup. When an iPhone is lost or stolen, the owner activates a “Find My” session remotely, usually through another authorized device connected to iCloud, which creates a time-limited access token.This token grants temporary but powerful administrative rights—such as triggering a remote lock or initiating a find command. Without this session, full system deletion or real-time tracking is restricted, underscoring the importance of securing login credentials after initial device setup. < disappointed but specific insights briefly emphasized here._p> What happens under the hood? - The iPhone enters “Find My Mode,” a state visible to authorized users and administrators.
- A unique session token is issued, encrypted and tied to both user identity and device ID. - This token expires automatically after 30 days unless renewed, enforcing strict security. - Located devices remain accessible for tracking and remote action within and across global servers.
This system balances user empowerment with robust safeguards, ensuring only recognized individuals can reclaim or monitor devices. The log-in session acts as a digital keyshell, protecting personal data while enabling urgent recovery. Advanced features like automatic “Find My” triggers—such as when a phone detects theft—can initiate this process with minimal user input, highlighting innovation designed around real-world urgency.
Step-by-Step Guide to Log Into Find My iPhone
Accessing your device through Find My iPhone log in begins with verifying identity and credentials.Here’s a clear, practical breakdown:
- Confirm ownership: Ensure the device is registered to your iCloud account. Log out if others hold Drivor access, and verify iCloud-booking details align with your profile.
- Connect to a trusted device: Use an iPhone, iPad, or Mac connected to Wi-Fi or cellular data.
For Macs, ensure Remote Desktop is enabled; for iPhones, iCloud.com or the Find My app is essential.
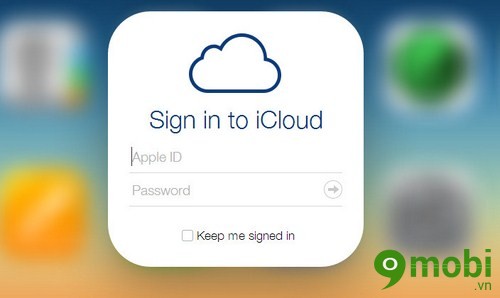
- Sign in with Apple: Enter your Apple ID and password. This step activates the session token—critical for unlocking Find My features.
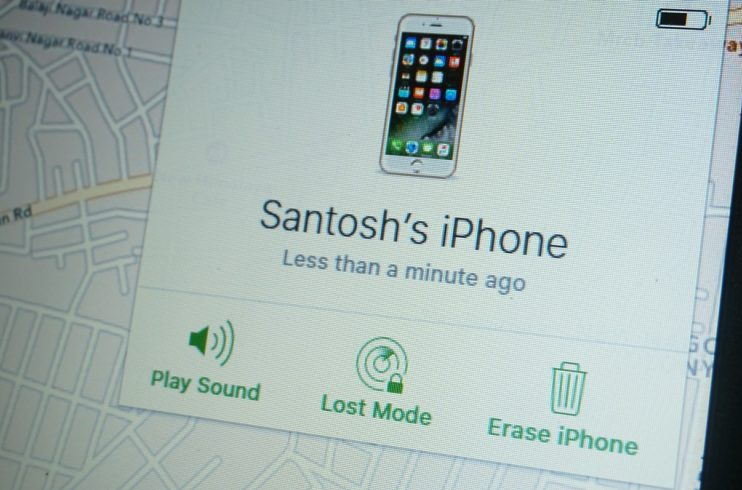
- Access your iPhone via iCloud.com or Find My app: Navigate to iCloud.com/find, or open the Find My app, enter your Apple ID, and locate the lost device. From here, invoke the “Find” or “Renew Find” to manage sessions or initiate a remote lock.
- Confirm session status: The interface displays the device’s location on a map, battery status, and last known activity, verifying active remote access.
Technical Deep Dive: Security, Privacy, and Forensic Utility
Beyond convenience, Find My iPhone log in integrates strong cryptographic and privacy principles.
Every session uses end-to-end encryption, ensuring data travels securely between device and iCloud. Apple maintains no direct access logs of sessions beyond what’s necessary, preserving user confidentiality. In legal and forensic contexts, authenticated Find My interactions leave traceable, admissible records—critical for recovering devices in disputes or investigations.
“The system prioritizes detection and response while minimizing user exposure,” says cybersecurity expert Dr. Elena Torres. “Authentication layers ensure only verified users trigger remote actions.”
Privacy as a Design Pillar: - Sessions expire automatically, preventing misuse.- No device identity or location data is exposed except to authorized locking or lockdown commands. - Apple’s zero-log policy on failed attempts protects users from phishing or unauthorized access.
Common Scenarios and Real-World Impact
Find My iPhone log in proves indispensable across common recovery scenarios.
Whether a device drops during travel, slips into a child’s pocket, or ends in a break-in, the system delivers actionable power:
- Clients searching for lost business iPhones: Companies using device tracking save operational disruptions—remote locking halts data exposure, and real-time location retrieval accelerates recovery.
- Parents protecting children’s devices: Parents leverage iCloud sessions to locate mis

:max_bytes(150000):strip_icc()/007_set-up-find-my-iphone-2000769-ba86a1513f1f4efb918d309ff35cb6f4.jpg)
Related Post

Define Rainbow Kiss: The Celebrated Symbol of Love, Unity, and Cultural Reverence

Stairway to Heaven: How Stairway To Heaven Korean Drama Sparks Emotional Metamorphosis in Viewers

