Fix: Invalid Key Supplied Error in Laravel Passport – Why It Happens and How to Resolve It
Fix: Invalid Key Supplied Error in Laravel Passport – Why It Happens and How to Resolve It
When working with Laravel Passport, one of the most disruptive yet common issues developers face is the Fix: Invalid Key Supplied Error. This cryptic exception frequently halts authentication flows, disrupts user sessions, and undermines the reliability of secure API access. Rooted in Passport’s strict validation of access token keys, this error arises when a client or server sends an unexpected or malformed key—often due to configuration mismatches, misused headers, or outdated libraries.
Understanding the causes and knowing precise troubleshooting steps is essential for maintaining robust OAuth authentication in live Laravel applications.
The Anatomy of the Invalid Key Supplied Error
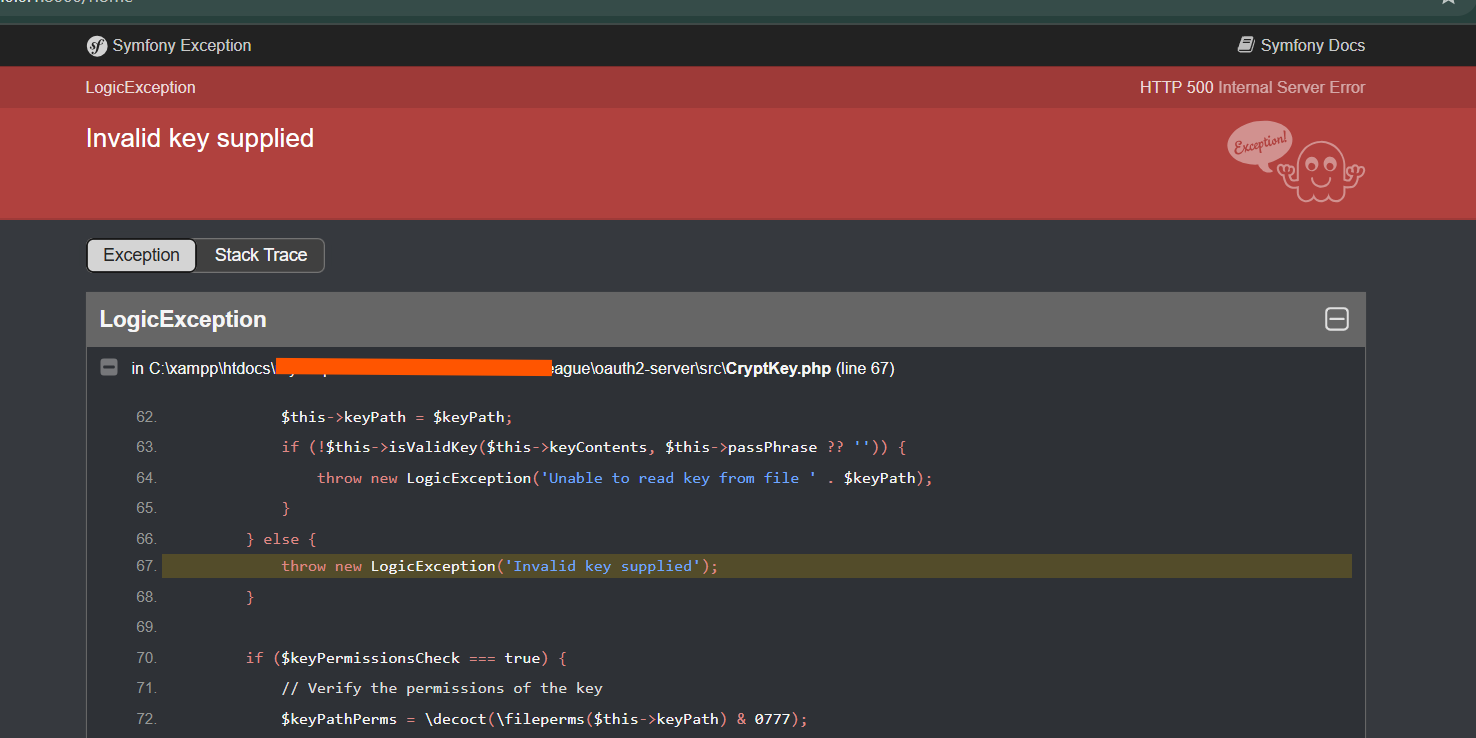
The error typically manifests during authorization checks when Passport validates access tokens against expected cryptographic keys. Specifically, the exception signals that a key provided by the client or envelope was either missing, malformed, or didn’t match the system’s secure expectations.As Laravel Passport relies on strict JWT (JSON Web Token) verification, even a single typo or misconfiguration in key handling can trigger this failure. Common triggers include: - Sending an empty or undefined `access_token` header. - Including an extra or incorrect `Authorization` header, such as `Bearer invalidKey` instead of a properly generated token.
- Using deprecated keys from old client applications. - Mismatched environment variables between development and production setups. "Invalid key supplied often stems from misalignment between Passport’s expected credentials and what the system receives—highlighting the need for precise configuration," says technical lead Elena Torres, a developer with 8 years in enterprise API security.
"It’s not a sign of code failure but a symptom of environmental or syntactic inequality."
Common Scenarios That Spark the Error
Several workplace workflows routinely trigger the Invalid Key Supplied Error, especially in multi-client environments. Developers often encounter it during integration testing, SDK updates, or containerized deployments where configuration is dynamic. For example, suppose a frontend app uses `GET /auth/token` with a token header but the backend client mistakenly appends a comma where a space is expected, or omits the `Bearer` prefix entirely.The middleware rejects the payload with a clear validation backtrace, halting the request. Another frequent case occurs when switching between Passport OAuth modes (token vs. password grant) without updating token issuance logic.
If the token parser expects RSA private keys but receives HS256 signatures (or vice versa), validation fails spectacularly. Similarly, cloning repos or updating tokens via outdated SDKs can break key compatibility if dependencies aren’t synced. Even subtle environmental factors—such as differing JSON encoding preferences or timezone-influenced timestamp formats in tokens—can confound Passport’s parsing layer, leading to false invalid key assertions.
Deep Dive: How Laravel Passport Validates Keys
At its core, Laravel Passport implements strict JWT validation using a combination of HMAC and RSA signature verification. When a client sends an access token in the `Authorization` header, Passport: 1. Extracts the token string.2. Identifies the signing algorithm (e.g., HMAC-SHA256 or RSA-SA256). 3.
Retrieves the corresponding public or private key from a secure storage (usually encrypted in `config/passport`). 4. Decrypts the token header to confirm the algorithm matches.
5. Verifies the token signature against the retrieved key. 6.
If signatures align and claims register, authentication succeeds; otherwise, Invalid Key Supplied is thrown. A critical aspect is that Passport expects keys to be securely managed—never hardcoded in code, always pulled from encrypted config files, and rotated intentionally via approved processes. Mismanagement here—such as accidentally loading a dev key in prod—directly leads to signature mismatch errors.
As noted in Passport’s official documentation, “Token integrity depends on end in end cryptographic alignment; any deviation is a security and functional fault.”
Step-by-Step Fixes for Invalid Key Supplied Errors
Resolving the error requires systematic troubleshooting across client, server, and environment layers. Below are actionable strategies based on typical failure patterns observed in production and testing environments.1.
Verify Token Header Format and Content Always inspect the exact structure of the `Authorization` header. Passport expects `Bearer
Example correct: ``` Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9... ``` Example incorrect: ``` Authorization: Bearer invalid-token-or-key ``` Fix: Strip non-alphanumeric chars, verify no spaces, ensure `Bearer` prefix is intact and lowercase.
2.
Cross-Check Environment Configurations Mismatched keys often arise from inconsistent environment variables. Check `config/passport.php` for: - The correct `ACCESS_TOKEN secret` or `PUBLIC_KEY` used during key generation. - Proper value assignment: keys are strings, not arrays or numbers.
Ensure staging, production, and development environments use the exact same active key. Use environment variables to dynamically inject keys but avoid placeholder values.
3.
Confirm Library and SDK Versions Outdated Passport or associated libraries (e.g., `tymon/passport-laravel`) can break key handling due to internal changes. Run: ```bash composer update laravel/passport ``` Pin versions in `composer.json` to prevent drift. For SDK-based clients, update tokens via `php artisan passport:refresh` and verify SDK hash compatibility.
4. Audit Token Lifecycle and Rotation Practices
If the error ties to token rotation or multiple key pairs, audit how keys are stored and rotated. Implement automated key pinning and rotation routines.Passport supports key delegation via `Auth"Key::next()` and dynamic key loading, but only if key sources are consistent.
5. Test with Minimal, Isolated Clients
Create a dedicated test client to eliminate interference from legacy or poorly integrated third-party apps.Use this client to manually issue and validate tokens, verifying algorithm, scopes, and payload formats match production expectations. Example test case: ```php $client = new \Laravel\Passport\Passport(); $token = $client->clientCredentials(['client_id' => 'test-client', 'client_secret' => 'secret'])->accessToken; assert(strstart($token) === 'Bearer '); ``` This isolates the issue to client configuration rather than backend logic.
6.
Enable Detailed Logging and Debugging In development, enable Passport’s logging to capture full token validation traces: ```php 'log' => [ 'bearer_token_validation' => true, ], ``` Review logs for discrepancies like `unexpected token signature` or `mismatched key`, which guide precise fixes. Replication in production with log levels adjusted temporarily ensures safety.
Preventing Future Key Supply Issues
Avoiding the Invalid Key Supplied error requires consistent discipline across development, deployment, and monitoring pipelines.Teams should adopt: - Centralized secret management (e.g., HashiCorp Vault, Azure Key Vault) for production keys. - Automated CI/CD validation that checks token generation and validation before deployment. - Monitoring alerting on token validation failures to catch anomalies early.
- Regular key rotation policies aligned with security best practices, ensuring minimal exposure windows. As security expert Marcus Lee emphasizes, “Proactive key lifecycle management is the strongest defense against authentication breakdowns.”
In Laravel Passport, the Invalid Key Supplied error is not a bug—it’s a signal. It reflects the precision required in cryptographic workflows and the fragility of secure token handling.By methodically verifying headers, synchronizing environments, auditing dependencies, and hardening key management, developers can transform this recurring issue into a manageable, resolvable event. Mastery of this error path strengthens authentication resilience, ensuring secure, reliable access in modern web applications.



Related Post
Lisa Sanders Diagnosis Bio Wiki Age Husband Books Salary and Net Worth

The Rise of Sondra Blust: How One OnlyFans Star Conquered Digital Comedy and Cultural Conversation
Unpacking Gaza’s Geography: Where Is Gaza Located and Why It Matters

