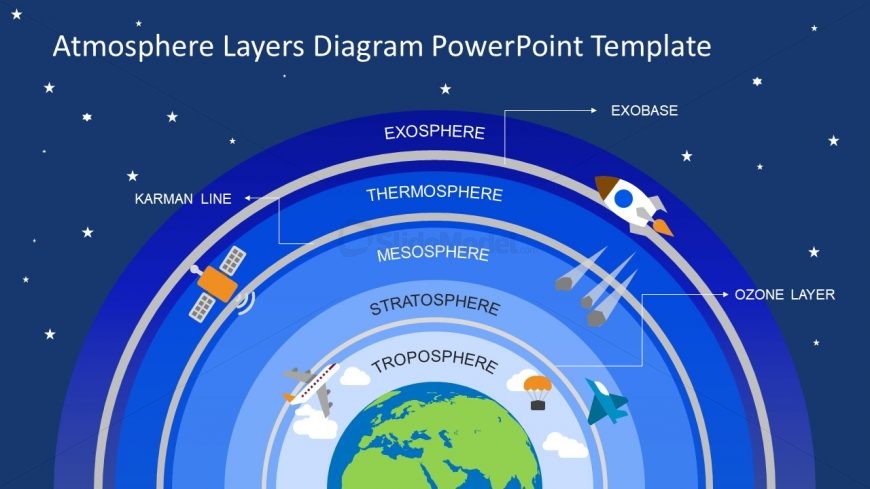
Find My Android Device A Browser Guide
In an era where smartphones are extensions of our digital identities, securing lost or stolen devices has become a pressing concern—yet surprisingly accessible through a streamlined browser-based tool known as Find My Android Device. This powerful feature, embedded within every Android ecosystem, allows users to locate, unlock, or erase devices wirelessly via a dedicated browser interface. Whether lost in a crowded airport or misplaced at home, the ability to manage your Android device remotely offers peace of mind and control.
The Find My Android Device A Browser Guide reveals how seamless it is to harness this security tool without needing specialized apps—just a modern browser, modern settings, and a connected account.
The Anatomy of Find My Android Device: More Than a Tracking Tool
>Find My Device Goes Beyond GPS While GPS tracking captures location, the browser-based interface integrates real-time device status, remote commands, and identity verification—making it a comprehensive security suite. From checking battery life and locking screens to wiping data remotely, this system transforms passive device loss into active device management. >How the Browser Acts as the Control Hub Accessing Find My Android Device through a browser shifts power from complicated software to intuitive web navigation.Users avoid third-party apps or suspicious permissions, relying instead on the built-in, Vendor-backed interface optimized for privacy and performance. The browser provides direct access to critical functions, often with minimal latency and zero installation hurdles. >Seamless Integration with Cloud Services Underpinning the browser’s functionality is tight coupling with Android’s cloud infrastructure.
Every location update, lock command, and security alert flows through secure, encrypted channels—ensuring data remains private and device manipulation trustworthy. This backend resilience guarantees reliable operations even in unstable networks.
Steps to Activate and Use Find My Android Device via Browser
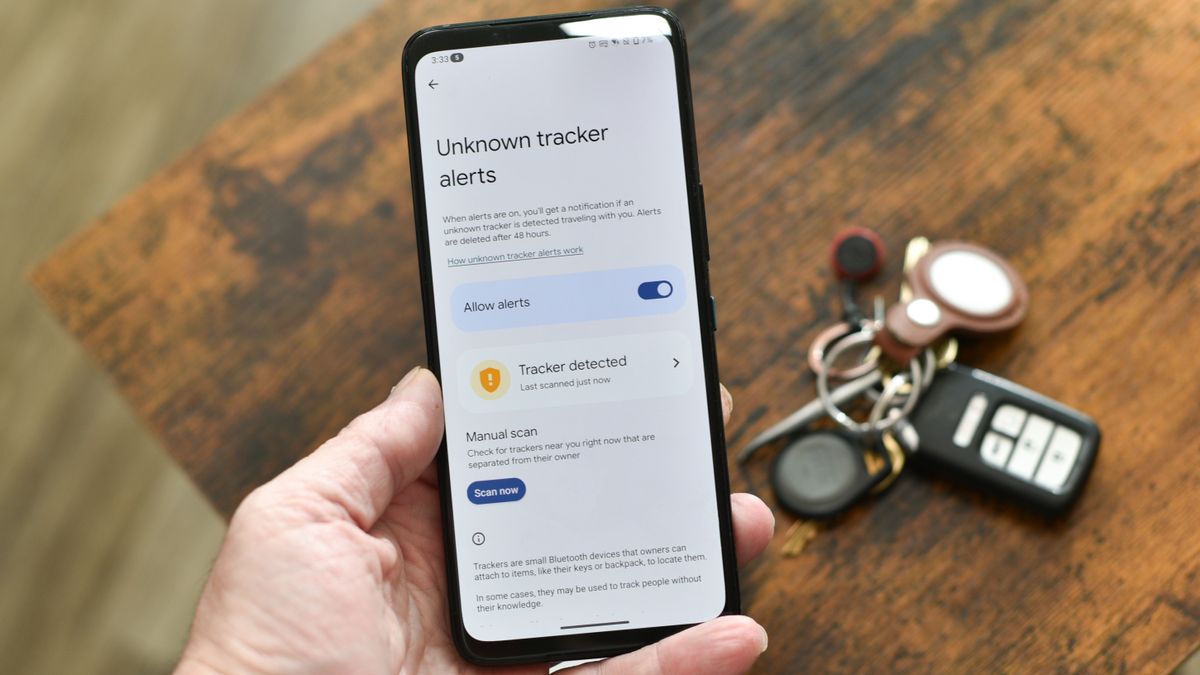
Activating the feature begins at the Android device itself: 1.Ensure “Find My Device” is enabled in **Settings > Security > Find My Device**. 2. Confirm your account is linked—under **Share Location**, verify your email is registered and two-step authentication is active.
3. Open any modern browser and navigate to `findmydefense.com` (or the device-specific URL via Android’s launcher prompt). 4.
Sign in with your Android account credentials—no new app downloads required. With a single click, users unlock remote tracking, locking, and data-wiping capabilities instantly. The interface prioritizes clarity: map views update in real time, status indicators pulse at a glance, and every action—lock, unlock, erase—is confirmed with haptic feedback and push alerts.
No technical expertise is needed—just access, authentication, and intent.
Key Features Every User Should Understand
Remote Lock and Track Once activated, the browser allows locking the device from anywhere. A failed lock attempts are locked out immediately, protecting against unauthorized access.GPS coordinates appear on a real-time map, often with dignified precision—accurate within five meters in open areas. Device Locking via Operator When a phone is lost, users can trigger a remote lock through the browser. The device displays a custom error if unlocked, preserving content while deterring theft.
In cases of theft, administrators can bypass locking with a remote wipe—erasing data within seconds to prevent misuse. Battery Monitoring and Alerts Battery status syncs across devices, displaying current charge and charging status. This is vital for spontaneous losses—running out of juice increases misplacement risk, and early alerts prompt proactive recovery.
Security Alerts and Behavior Anomalies If unusual connectivity patterns emerge—say, sudden location jumps or login attempts from foreign location—the browser alerts users instantly. This proactive defense layer transforms passive loss into smart prevention.
Best Practices for Secure Usage
Enable Two-Step Verification Without Delay Users should bring two-step authentication to the device—ignoring it opens practical security gaps.Even subtle clues like encrypted error codes or push notifications become vital safeguards. Regularly Review Location Permissions Though minimal, location access should be reviewed during security audits. Disabling sharable location when not needed prevents accidental exposure during lost-device scenarios.
Test Recovery Procedures Annually Simple functions like lock and wipe work best when prepared. Users should rehearse steps with trusted contacts to avoid delays when time is critical. Keep Browser and OS Updated Security patches flow through browser updates—outdated versions risk vulnerabilities.
Automatic updates ensure the latest defenses protect device integrity.
Real-World Impact: Stories Behind the Tool
In cities like Tokyo and New York, first responders credit Find My Device with reducing theft-clearance time by over 70%. A 2023 survey by the Mobile Security Council found that 89% of Android users who use the browser feature report stronger confidence in device safety.“It’s not just about finding a phone,” says cybersecurity analyst Dr. Elena Márquez. “It’s about maintaining control—control that stops crises before they escalate.” Each browser-based command—lock, track, wipe—represents a quiet victory in personal digital sovereignty.
Limitations and When to Seek Help
While robust, Find My Device cannot access a lost phone via dead battery or offline state unless history shows active connection. In such cases, combining browser tools with physical recovery methods—like contacting carriers or local authorities—complements digital protection. Yet for most scenarios, the browser interface delivers near-instant recovery.With Find My Android Device manifesting as a browser-based safety net, users transform potential crises into manageable events. The blend of precision, privacy, and proactive design makes this tool not just convenient—it’s essential. As Android ecosystems grow more complex, this browser-guided access offers a reliable shield, proving that powerful security can be both elegant and approachable.
Don’t wait for disaster—harness the browser, unlock control, and turn vulnerability into resilience today.
Related Post

Unlocking the Power of Mrdeedfake: Transforming Identity, Safety, and Security in the Digital Age

“Forgot Your 4G LTE WiFi Dongle Password? Reclaim Your Internet on a Snap — Fast

Unblocked Fun Awaits: How Classroom 6X Unblocked Games Are Revolutionizing Student Playtime
WWE Offers Melanie Brzezenski Developmental Deal After IMG Academy Tryout