Disabling Core Isolation and Memory Integrity in Windows: Controlling the Firewall Against Exploits
Disabling Core Isolation and Memory Integrity in Windows: Controlling the Firewall Against Exploits
Windows 11 and later versions incorporate advanced security mechanisms to protect system integrity and data resilience, two cornerstones increasingly targeted by sophisticated malware and advanced persistent threats. Among the most potent defenses are Core Isolation and Memory Integrity—critical features designed to shield critical system processes from unauthorized manipulation. While these safeguards greatly strengthen security, legitimate administrators and security professionals sometimes seek ways to disable them, whether to optimize performance, enable legacy software compatibility, or conduct low-level system audits.
Understanding the mechanics, implications, and responsible use of disabling Core Isolation and Memory Integrity is essential in today’s complex threat landscape.
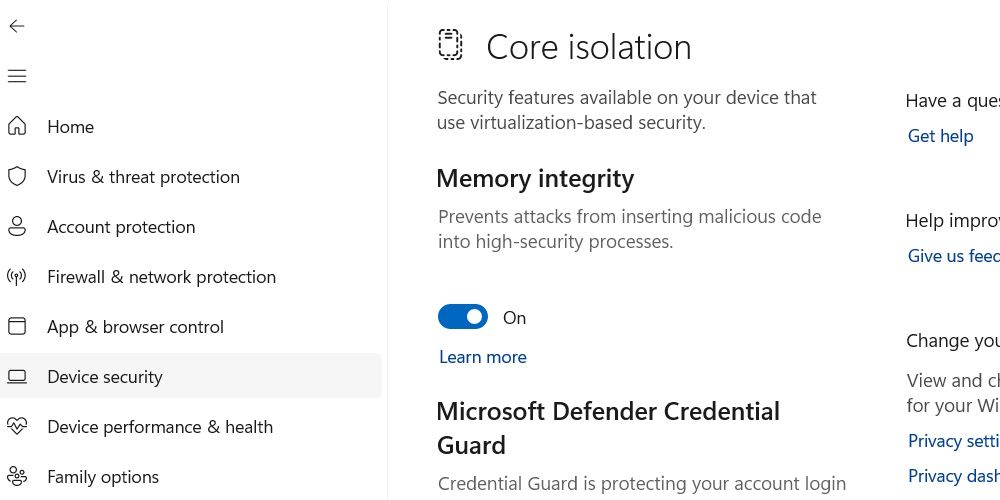
Core Isolation and Memory Integrity represent fundamental pillars of Windows’ defense-in-depth strategy, designed to secure system-critical operations and prevent code injection at the most granular level. Core Isolation isolates privileged kernel-mode processes from user-space applications and less trustworthy components, ensuring that exploitation of internet-facing services cannot cascade into system-wide compromise.
Memory Integrity, meanwhile, leverages hardware-enforced memory protections—including Control Flow Enforcement Technology (CET) and Data Execution Prevention (DEP)—to block common attack vectors such as buffer overflows and return-oriented programming (ROP) attacks. “These protections are not merely perimeter defenses—they actively rewrite how memory is handled at runtime, making exploitation far more difficult, if not impossible,” explains cybersecurity researcher Dr. Elena Vasquez of AnalystSec.
“They enforce correct execution paths and detect invalid memory access in real time, effectively turning the processor itself into a security enforcer.”
Disabling Core Isolation strips away a vital layer of privilege separation between system trust levels. This affects features like BitLocker recovery mode, system file protection, and secure boot integration, which rely on isolated kernel operations to function safely. Without Core Isolation, user-mode applications gain broader access to system internals, increasing the attack surface and potentially allowing persistent rootkits or privilege escalation exploits to survive reboots.
Microsoft’s official documentation clearly identifies Core Isolation as mandatory for secure Windows updates and bioshell resistance, reinforcing its role beyond optional tuning. Similarly, Memory Integrity enforcement ensures that no unauthorized code executes in protected memory regions. Tools like Windows Memory Integrity leverage the processor’s enablesec resource—anchored in Secure Execution Technology (SET)—to monitor memory access patterns with minimal performance impact when properly tuned.
For standard consumer use, this feature operates quietly in the background, enforcing strict memory safety policies that prevent code reuse and unprivileged execution. However, disabling Memory Integrity disables real-time enforcement of these rules, opening the door to timestamped attacks and zero-day exploits that bypass traditional sandboxing.
Administrators may disable these protections under specific, controlled scenarios.
Legacy applications—particularly those written before memory safety became a design priority—may fail under Core Isolation, where direct kernel interaction conflicts with process isolation models. Automation scripts, debugging tools, and virtualization platforms sometimes disable Memory Integrity temporarily to inspect kernel memory or bypass security checks during development. But such actions carry inherent risk: reducing system resilience and increasing vulnerability to exploitation.
“Every disableété reduces the operating system’s inherent ability to thwart exploitation,” warns cybersecurity firm Mandiant’s threat analyst Marcus Trent. “It’s not a patch—and certainly not a feature for widespread use.”
- Assess Necessity: Evaluate whether the disabling is truly required—such as resolving software conflicts or validating system behavior during security research. Document rationale thoroughly.
- Test in Controlled Environments: Apply changes only in isolated test labs or staging systems, never production environments without extensive validation.
- Limit Scope: Apply protections at the least privileged level—disable Core Isolation only for specific trusted processes, not the entire system.
- Monitor for Anomalies: Enable enhanced logging and intrusion detection to catch suspicious activity that may arise from reduced memory safeguards.
- Revert Promptly: Once the objective is achieved, restore protections immediately to maintain baseline security.
While performance gains or compatibility fixes may tempt users, disabling Core Isolation and Memory Integrity undermines the core defense architecture built into modern Windows.
These features are not incidental—they are engineered to stop attacks at their source. Rather than removal, security-conscious approaches favor targeted configuration adjustments, leveraging enclave technologies like Windows Subsystem for Linux (WSL) with secure kernels or using virtual machines to isolate untrusted workloads. In doing so, organizations preserve both functionality and protection, ensuring that Windows remains a hardened platform in the face of evolving threats.
Ultimately, the decision to disable Core Isolation and Memory Integrity demands careful judgment.
For routine users or even expertise-prone IT teams, missteps could render systems exposed to sophisticated adversaries. As threat actors continuously refine evasion techniques, understanding the deep integration of these features is not just for security professionals—it’s vital knowledge for anyone managing or securing Windows environments. By respecting their design purpose and applying them thoughtfully, users maintain a balance between operational needs and robust defense.
In the ongoing battle between system security and exploitation, knowing when—and how—not to disable these safeguards defines responsible computing in the modern era.

Related Post

NZ Post in Palmerston North: Your Essential Guide to Staying Connected Across New Zealand

Selena Gomez’s Parents: A Deep Dive into the Family Background Behind the Star
2007 Infiniti Q50 Owners Are Furious Over a Hidden Design Flaw That Compromises Safety and Style

Joanna Rosen: A Comprehensive Insight Into Her Life and Career

