Barer Or Bearer: The Critical Choice Behind Secure Token Authentication
Barer Or Bearer: The Critical Choice Behind Secure Token Authentication
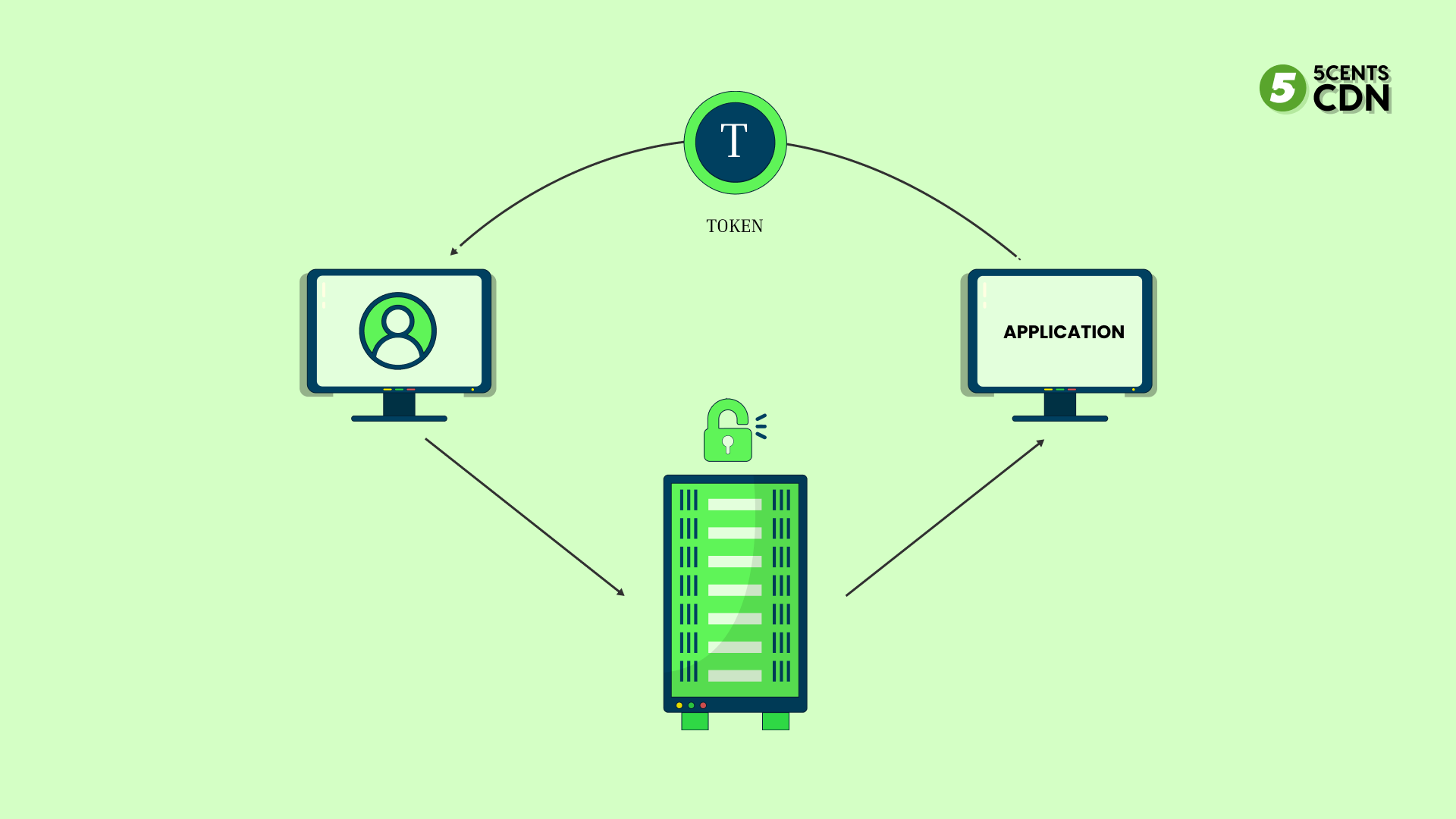
In the evolving landscape of digital identity and access control, organizations face a pivotal decision: whether to issue security tokens as plain “barers” or fortified “bears.” This distinction profoundly impacts authentication strength, vulnerability exposure, and compliance readiness. Bearer tokens—essentially unprotected credentials handed directly to users—offer simplicity but demand rigorous safeguards, while barer tokens, by design, cannot be misused without direct possession, reducing certain attack vectors but introducing logistical challenges. Understanding the nuanced trade-offs between barer and bearer tokens is essential for architects, security teams, and developers navigating identity management in modern applications.
At the core of this comparison lies the definition: a barer token functions as a raw credential that must be preserved—its exposure means automatic user authority until revoked. In contrast, a bearer token is explicitly engineered to diminish misuse; typically time-bound, scoped, and encrypted, these tokens require secure transmission and storage to prevent unauthorized access. “Bearer tokens shift liability from permanent exposure to temporary trust,” explains Dr.
Elena Torres, lead cryptographer at Global identity firm FortifySecure. “While barer tokens place full responsibility on the user’s device or session, bearers trade simplicity for enhanced runtime protection—foundational to modern zero-trust frameworks.”
The Security Implications of Barer vs Bearer Tokens
For instance, OAuth 2.0 bearer tokens frequently incorporate Short-Lived Access Tokens (SLATs) and refresh tokens with longer but still bounded lifespans, reducing persistence. Systems adopting bearer tokens often layer additional safeguards—such as IP binding, device fingerprinting, and multi-factor authentication at issuance—creating defense-in-depth strategies. Conversely, barer tokens—often analogous to direct access passes—create inherent risk.
Without built-in expiration or scope limits, a stolen barer token remains valid until revoked, requiring immediate invalidation to prevent abuse. A 2023 report by the Cybersecurity & Infrastructure Security Agency (CISA) noted that 38% of unauthorized access incidents involved unprotected or weakly protected bearer credentials due to inadequate token rotation practices. “Barer models demand relentless monitoring,” warns cybersecurity analyst Marcus Lin.
“You can’t assume a token is safe just because it hasn’t changed hands—every exposure is a permanent breach risk until terminated.”
Yet barer tokens maintain relevance in constrained environments where user trust and system simplicity outweigh scalability. Machine-to-machine (M2M) communication, legacy system integrations, and high-frequency API requests often benefit from the reduced overhead of simple, short-lived barer credentials. In these contexts, strict access controls—enforced through network segmentation, encryption, and role-based privilege assignment—offset latent vulnerabilities.
Operational Use Cases and Deployment Realities
Organizations deploy barer and bearer tokens across distinct operational tiers. In enterprise identity ecosystems, bearer tokens dominate single sign-on (SSO) platforms and API gateways where seamless user experience balances security. For example, fintech firms using bearer OAuth tokens enable customers to access multiple services under a single secure session, with automatic token expiry and refresh capabilities managed via centralized identity providers.By contrast, barer tokens thrive in edge computing and IoT environments, where devices operate intermittently and manual intervention for token revocation is impractical. A sensor network collecting industrial data, for instance, may issue short-lived barer credentials to each node—limiting each device’s privileged window while avoiding the complexity of token refresh protocols. “We encrypt the token and store it only in hardware security modules,” notes DevSecOps specialist Raj Patel.
“That way, even if intercepted, misuse is contained to minutes, not months.” The integration of modern authentication standards like OpenID Connect and FIDO2 further shapes token strategy. Bearer tokens often complement biometric authentication—tying device possession and identity verification to cryptographic proof—while barer models benefit from continuous authorization checks that reassess privilege in real time. “The future leans toward adaptive tokenization,” Lin observes. “Not just barer or bearer—but context-aware tokens that evolve based on location, behavior, and risk score.”Comparative Summary of Token Models
Compliance, Risk Mitigation, and Best Practices
Regulatory frameworks such as GDPR, HIPAA, and NIS2 place stringent demands on how identity credentials are managed. Bearer tokens, when properly implemented with encryption and expiration logic, align closely with principles of data minimization and defense-in-depth. Yet failure to revoke or rotate barer tokens promptly can trigger non-compliance penalties.
Standards bodies including NIST emphasize that token lifecycle management—not token type alone—is critical. Best practice demands a risk-based approach. Organizations should: - Limit barer tokens to low-privilege, time-restricted access where feasible, and pair with behavioral analytics.
- Enforce ticketing and encryption for bearer tokens across all transmission channels. - Automate token rotation and employ short half-lives where possible, even for barers. - Integrate unified identity platforms to monitor token usage and detect anomalies in real time.
“Token strategy must evolve with your threat model,” Patel concludes. “Choosing between barer and bearer isn’t binary—it’s part of a broader security ecosystem demanding precision, not prejudice.” In an era where digital trust is fragile and attack surfaces vast, the choice between barer and bearer tokens is far from symbolic. It is a deliberate architectural decision that shapes how securely an organization protects access, data, and reputation—one that demands clarity, foresight, and disciplined execution.



Related Post

Revolutionizing Digital Collaboration: How 9Xbuddy is Transforming Team Productivity Across Industries

IStore Nelspruit: Your Ultimate Guide to Apple Prices & Market Trends in Greater Nelspruit

Fantastic Four 2017: A Gateway Superhero Film That Missed the Cosmic Mark

IDFA Funds Explained: Mastering Capital Gains Estimates in Digital Advertising

